Enjoy Your Best Vacation At Douala-Flights From Dubai To Douala Cameroon!

Cameroon is a country in Africa and Douala is a city of Cameroon and it is the capital city of Littoral region. Cameroon is on the banks of Wouri river. Douala is a large city having seven districts under its fold. It is the economic capital of the country and it is a famed commercial centre of the country. The city is witnessing fast development and the economy of the city is termed as the best performing economies of Africa.
Douala houses the largest port of Africa and Douala international airport of the city is a major airport. Akwa one of the important districts of Douala is a prominent business and commercial centre. Douala is a safe city to visit and it has many attractions.
When Should You visit Douala?
The city experiences tropical monsoon climate and July and August are the cooler months. So, you can choose these months to visit the city.
Get Around
You can hire taxi cabs to hop from one destination to another and in case you would like to save money choose shared taxi cabs. You can choose such cabs when your co traveller is also visiting the same destination.
Tourist Attractions In Douala
Douala is famous for its beaches and some other historical attractions. Some of the attractions of the place are
Kribi
This is one of the best beaches of Cameroon and you can spend time leisurely at this beach. The beach side restaurants offer best sea food varieties.
Marche Des Fleurs
If you are interested in buying souvenirs and artefacts then this is the place to be visited. The colourful display of handicrafts is indeed an attraction and you can purchase best handicrafts of the region at this place.
Parcours Vita
It is a sports park and it has a gymnasium, running track and hiking routes. Fitness freaks must visit this place as it has facilities for soccer and cycling.
The city has some famous museums and other attractions. You can visit the museums to learn more about the land.
Flights
The aerial distance between Dubai and Douala is 5771 kms and there are no direct flights on the route. The travel time with a connecting flight with one stop over is 11 hours 25 minutes. Tuesdays and Wednesdays are considered as the cheapest days to fly to Douala. You can search travel sites to get info on carriers, ticket prices, number of stop overs and cheapest tickets. Air France, Egypt Air, Rwand Air, Kenya Airways, Turkish Airlines and Ethiopian Airlines are the flights from Dubai to Douala Cameroon.
Valuable Information
You can get cheap tickets when you book at least three months in advance through a travel site. The travel sites announce discounts and cash backs regularly and using them you get much cheaper tickets for Dubai to Douala Cameroon flights. 15 flights fly on the route in a week. The ticket prices for connecting flights is around 2,680 AED and the airport code of Dubai is DXB and that of Douala is DLA.
Paperstyle Whatsapp Wedding Invitations: Go With The Trend!

Paperstyle Whatsapp Wedding Invitations
Individuals send messages and videos to their friends and relatives through whatsapp. Whatsapp is now used to send wedding invites too. Earlier getting paper cards printed and delivering them personally was the only option. You spend a lot of money on printing, logistics, postage, courier errors, etc. Today when you have so many other options why cling on to the old one. You can send your invites through whatsapp to as many people as possible and you will start getting congratulatory messages immediately.
This invite is preferred as it is convenient to send and if you have a fascination for eco friendly products then this is for you. Paperstyle whatsapp wedding invitations are like the physical paper invitations and it has much more features. Getting it made is not difficult as the card designers will bring out the features which you want. It is not difficult to make and your card will remain unique and features rich if you go for some rare variety.
Variety In Paperstyle Whatsapp Wedding Invitations
Compared to paper invitations and the cost involved in sending these cards are cheaper and it involves only the initial cost. Once made these cards can be sent easily without any additional charge. You can choose from festive, royal processions, floral, diyas designs, cartoon, caricature, informal styles, etc. You can have as many pages as you wish in this invitation and you will find the whole process flexible. With the paper variant a lot of cost is involved until you go for the fair draft and each time it is time consuming but with this changes can be made easily.
Paperstyle Whatsapp Marriage Cards: The Much-Preferred Option
The colours and designs look very attractive as it is a digital format. You can even bring out your own designs through this invitation. Informal writing style could also be used for this invite. Nowadays, in these lockdown days people prefer this invite as marriages with a huge guest list is not preferred. For small marriage functions this is the best and paperstyle whatsapp marriage cards are preferred as it is cost effective.
Use Your Creativity
Making the invite is not time consuming as the designers have the required templates with them. There are many sites offering their services in making these invites and if you feel you can make your own invite and save money then this is the best option. There are many sites offering free tutorials which give you step by step instructions to make this invite. So, use your imagination and come out with something different.
How is HIPAA security Risk Assessment Done?

HIPAA security Risk Assessment
If you are a HIPAA compliant organization then you can get security risk assessments done. HIPAA is a standard for sensitive patient data protection which has to be followed by all involved in healthcare. Any medical practice, health insurance plan and third-party clearing house all have to follow the HIPAA mandates.
The data is stored and transferred in electronic form. It is important to prevent cyber attacks and keep the data and the systems secure. Any amount of leakage or damage can be critical for the business. Many companies make the HIPAA compliance a mandate for their projects. You can do a HIPAA security risk assessment to know about the status of the compliance implemented.
HIPAA assessment
The assessment companies help the clients to achieve their compliance goals. The assessment process is as follows:
The company will assess the main elements of the business and define the actions that need to be taken as per the business requirements.
Approved and certified auditors form the company take a look at the business processes, controls implemented and the existing business requirements. It is then compared with the requirement of HIPAA compliance.
The auditors will conduct an internal audit to determine the status of the implemented HIPAA controls within the business’s policy procedure requirements.
Practices followed in HIPAA compliance
Some of the common practices used in HIPAA compliance are as follows:
Creating policies for using the workstations, electronic media and data access points.
There should be a policy which restricts the adding, transferring and deleting data using any type of electronic media.
You should ensure that there is no data transferable device in the business premises.
Using access controls for the data that is present in the network.
Using user ids, access procedures, auto log off and encrypting the data.
Checking all those whom the access was granted and doing random checks of the data looked upon.
Auditing and maintaining logs on hardware and software platforms.
When you want to destroy data you should use the proper integrity controls and measures. The data should be destroyed completely. You should keep a disaster recovery team ready in case of a loss.
Taper Lock Bearing Locked to Provide More Stability And Strength
Taper Lock Bearing
In any automotive device or machinery, when a metal comes in contact with metal, friction is created. This causes wear and tear of the device and decreases its lifespan as well. Hence, to reduce the stress and friction between the metals, thrust bearings are widely used. These are available in various varieties, size, design, and dimensions. Ball thrust bearings and roller thrust bearings are very commonly used. For the applications which need higher load capacities, roller thrust bearings are in great demand.
Tapered Lock Bearing:
Amongst all the bearing, tapered lock bearings are commonly used in automotive machines. They have small rollers which are tapered and arranged to converge the axes of the rollers at a point on the bearing’s axis. Very carefully, angle, length, and diameters of rollers are calculated so as to get the correct taper. This allows smooth movement of the rollers on the face of bearings without any skid. Double row taper roller bearing possesses higher stiffness and load carrying capacity.
The taper lock bearing design is used in various applications and is available in various sizes and dimensions. For instance, in the roller thrust bearing, washers that are used are flat while in the ball bearing, they are mostly grooved. Hence, they offer greater axial rigidity and frictionless movement of higher loads. The roller thrust bearing is composed of rolling elements which can be cylindrical, spherical, tapered or needle rollers. They are generally used in cars between rotating shafts, gears, etc as the rollers carry high amounts of axial loads. An oil-based lubricant is used and hence this type of bearings provides greater stability along with speed rate.
In roller thrust bearing, the rollers length is kept perpendicular with respect to the shaft. They are available in a plethora of shapes and sizes that affect the efficiency of these bearings directly. The roller bearings consist of two rings which are also popularly called as ‘washers. These washers are configured with various sizes, designs, and shapes of the bearings.
Mechanism ofTaper Lock bearing:
The taper lock bearing mechanism works on a very simple and easy mechanism. These bearings are assembly lockable onto a shaft, the assembly contains a first and second tapered adapter that defines axial bore and has an outer, annular tapered surface. This helps to keep the device in forwarding direction without causing any type of friction or stress.There are many types of bearings, but the tapered bearings are very popular for a varied number of applications. The tapered bearings have conical rollers and are.
Understanding Standards of PCI SSF compliance and Need for PCI SSF compliance
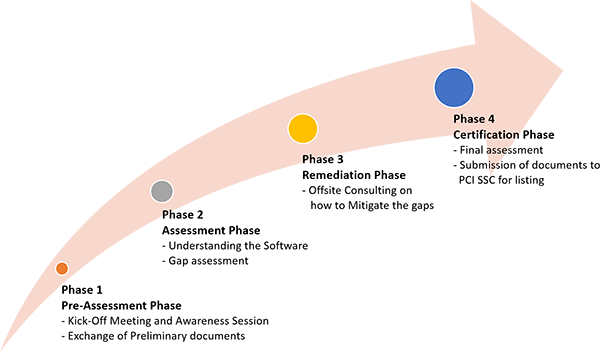
PCI SSF compliance
As many people think that making payments using the different portals or software is quick and easy, at the same time, there is an equal number of public worried about the risk involved in these type of payment options. For the safety of the customers, the PCI security standard council (PCI SSC) has set some framework that defines the standards to safeguard the public from breaches. These are the PCI Software Security Framework (SSF). The software used for the payment transactions should have the PCI SSF compliance that assures secured transactions.
Standards under PCI SSF:
The PCI SSC has designed two different standards under this framework that the payment software vendors should consider. It includes the validation framework with an additional qualification program designed for the assessors. The payment software should pass these standards to achieve PCI SSF compliance. These standards include:
PCI SSS: PCI Secure Software Standard is defined for the security requirements and procedures crucial to protect the confidentiality and integrity of payment data. It controls security controls, characteristics, features, and functionalities possessed by the payment software and has to be maintained throughout the software lifecycle. These standards are defined by the vendor.
PCI SLC: PCI Software Life Cycle defines the procedures and requirements for the vendors for validating the management of payment security during the entire software life cycle. It includes the technology, processes, and persons involved in the development, maintenance, and deployment of the payment software products and services.
Benefits of PCI SSF compliance:
Any person approves the use of any product or service based on the advantages or benefits offered by it. There are different benefits for any payment software if it has PCI SSF compliance. These benefits include:
Elimination of risk: If the payment software inconsideration has the PCI SSF compliance, then there are decreased chances of any unnecessary penalties or complications arising from the data breach.
Decreased chance of data brisk: If the software is PCI SSF compliant, then there is a decrease in chances of an attack on the software. This is due to the presence of suitable protection and security measures for the payment software.
Enhanced protection: The PCI SSF compliant payment software helps to ensure the customer that the software protects the critical data. It ensures that there is secure authentication and implementation of access controls.
Regulation: It ensures that all the legal obligations are met and all the regulations complied with.
Boost confidence: If the payment software has PCI SSF compliance, the customers and their stakeholders have good confidence in their products and services.
Enhance business: If the customer has confidence in the payment software, they continue to use it. This will help to increase the business and will also help in attracting more customers.
Considering all the above-mentioned benefits of PCI SSF compliance, the payment software must comply with the standards as it will ensure the customers having the best security while making the transactions.
How to Set an Ambience for Secure Software Development

The risks are bound to open up when the security problems are not addressed by an organization at the right time. Whenever you pass in sensitive data through the commercial systems, there is always a risk of data manipulation and mishandling.
Governments are now finding out the right means for maintaining data security measures. Imposition of fines can be explained when you overlook the fundamentals. Alongside checking the balance of quality, it is also important to develop the security apps.
Why Is Secure Software Development So Important?
Following the roadmap in a different way throws much light on your concern over safety of applications. Besides that, the span of secure software development also deserves special mention.
What Are the Current Forms of SDL Frameworks that We Use?
A few affiliations surrender and keep SDL strategies which totally try and adjust affiliations. Each strategy joins a careful once-over of common practices authentic for an alliance. They go with recommendations for getting the practices to communicate business necessities. You can take the approaches of SDL as arrangements for making safe and improved structures in your get-together.
So when a framework proposes express activities, you in any case everything find the opportunity to pick something that matches you best. For example: Does an application dispatched by you merge online pieces? Expecting this is the situation, and if the methodology recommends security making game plans for your social event, by then you ought to encourage raised getting ready on PCI going forward.
Standard SDL approaches are not appended to a specific stage and spread extraordinarily enormous practices comprehensively. Any of it will coordinate since it's the starting period of SDL at your alliance. It's a wise idea to examine each prior to picking an over the top decision, undeniably. You can in the said manner make another endeavor them to oblige your thing progress cycle.
SDL methodology can be divided into two solicitations: interesting and illuminating. Prescriptive method uniformly asks customers about all that they should perform. The "expressive" option states depictions of things that the various affiliations have turned.
Key Advantages of Secure Software Designing
High Security is a demanding factor. IN SDL, the continuous search for shortcomings renders easing out business risks and improving of application quality. The initial assumptions concerning the absentees linked with base level reductions are the points of checking and resolving of related issues. Secure software designing is supportive towards an updating of rules and laws associated with security. Inner security is improved when SDL can be incorporated with the internal coding contraptions.
The Whatsapp Wedding Cards Are Leaving a Mark on Our Minds for Good
The wedding market has now been flooded with online cards. Instead of narrowing down your choices, you may compare the wide range of features besides the adaptability of the online cards. Although you ought to show some amount of flexibility in terms of budget, it stands out against the odds. The extent of an individual’s capacity can be enhanced by exercising control over certain factors and making certain things necessary.
How the Market Needs Are Matched by Whatsapp Wedding Cards
Irrespective of how regularly you notice the idea, you are never going to do justice to a lot of plans and designs open for making cards except when you do some exploration. Each idea, segment, and subject that you like is adaptable and you get the wedding card you had always asked for.
Be it about including pastel tints, cherry blossoms, and a calligraphy literary style or a card reflecting your objective wedding spot, only the sky proves to be the end. They will without a doubt have a long-standing effect on your guests.
Skipping All Challenges with Whatsapp Marriage Cards
At the point when the traditional cards are printed, there comes the issue of genuinely passing on each and every message in a proper manner. While many card makers do offer the control of setting the card for you, it is still a huge scrappy structure and an outdated one. After you analyze the various levels of the customization, the Whatsapp wedding cards are sent to you and they really stand out.
Starting there on, you know how fundamental distribution of the online greeting cards occurs, especially over all the social stages like WhatsApp, Facebook or even a direct email. These web wedding invite cards similarly turn it easier for prospects to RSVP and evaluate their quality.
A plethora of reasons are there as to why the modern ladies and gentlemen prefer to go for the wedding cards online. The planning part still holds out among other things. It makes you cherish every move as you set time out for custom-making Whatsapp marriage cards.
